Unlocking web3’s full potential: A deep dive into Data Verifiability Protocols
Data Verifiability Protocols (DVPs) are transforming web3 by enabling secure, trustless, and scalable integration of real-world data by unlocking new innovation in web3 application.
Bitcoin, introduced in 2009, laid the foundation for the decentralized internet by pioneering blockchain technology and enabling trustless transactions without intermediaries.
Bitcoin catalyzed web3 but early innovations were limited by the challenge of accessing off-chain data
Early blockchain networks like Bitcoin were application-specific, designed for single use cases such as payments (Bitcoin), scientific computing (Primecoin), decentralized DNS (Namecoin) and private transactions (Monero). Though Bitcoin included a basic scripting language, which allowed innovators to experiment with new ideas. Between 2009 and 2015, innovators like Paul Sztorc, Erik Voorhees and Vitalik Buterin explored concepts like prediction markets, betting games(SatoshiDICE) and real world assets(colored coins) using Bitcoin's limited programming capabilities. However, the fundamental issue remained the oracle problem—how to securely bring off-chain data onto the blockchain for these use cases. In 2014, Dan Smith's proposed TLSNotary aimed to address this issue by leveraging internet standards like TLS. While it gained some traction in discussions on Bitcointalk, it has only recently gained significant momentum.
Ethereum’s smart contracts sparked a wave of web3 innovation leading to DeFi and advanced dApps
In 2015, Ethereum transformed the blockchain space by introducing smart contracts and a shared network allowing developers to build decentralized applications (dApps) without creating new blockchains for each use case. This simplification sparked the rise of web3 enabling innovations like DeFi, NFTs and decentralized governance. Smart contract platforms attracted developers but early applications remained simple due to limited access to off-chain data. The development of oracles triggered a cambrian explosion in innovation especially in DeFi, enabling complex financial products like DEXs, CDPs and lending platforms. More recently prediction markets have expanded use cases further.
Blockchain scalability and interoperability at its core are a data problem
Blockchains remained slow and faced significant scalability issues. The Bitcoin block size war (2015-2017) and Ethereum’s CryptoKitties congestion incident led to discussions around adjusting block size and the gas limits. At its core, both solutions were centered around “data”, aiming to crunch more transaction data into blocks. Even today, proposals like EIP-7781 continue to address scalability using a similar approach. As more blockchains emerged, each isolated with strong communities and fragmented liquidity led to a new problem: Interoperability. Solutions like Bridges and Layer 1’s like Cosmos and Polkadot addressing this problem emerged. At its core, interoperability is fundamentally a challenge of ensuring secure and trustless data communication between different chains.
Data is the key to web3 innovation
Data has been central to web3 innovation, driving both application development and addressing challenges like scalability and interoperability. While web2 benefits from abundant data, web3’s limited access to off-chain data has constrained its potential. The real challenge lies not just in bringing data on-chain but in doing so securely and trustlessly. This need has given rise to Data Verifiability Protocols (DVPs) which go beyond traditional oracle solutions, laying the foundation for trustless, secure and verifiable data integration. The next section will explore the shift from Oracles to DVPs and their transformative impact on the future of web3.
Oracles laid the groundwork but DVPs are the future of trust and scalability
Oracles have been pivotal in enabling dApps to access off-chain data, driving innovations in DeFi, prediction markets and more. By bridging the gap between web2 and web3 oracles allow smart contracts to respond to real-world events and spark new forms of decentralized innovation. However, oracles have only scratched the surface of what's possible in web3.
As web3 applications evolved it became clear that more sophisticated data requirements were emerging, revealing key limitations in oracles. Developers saw the need for more diverse data along with greater scalability and trustless verification, highlighting fundamental challenges in data handling.
Let's explore these three limitations in depth, starting with the distinction between public and private data.
Oracles handle public data well but private data is key to unlocking advanced web3 use cases
Oracles handle public data like market prices and sports scores well but many advanced web3 applications rely on private data—such as health records, credit scores, or social profiles. This data is crucial for unlocking use cases like under-collateralized lending, personalized DeFi products, secure identity solutions, insurance claims and private healthcare applications.
Integrating private data into decentralized systems presents significant security challenges. Blockchains are transparent by nature, making it difficult to protect sensitive data while maintaining confidentiality, integrity and provenance. Traditional oracles lack the cryptographic infrastructure to handle this securely, requiring advanced techniques to verify private data without exposing it. Without these enhancements, using private data on-chain risks compromising both security and user trust.
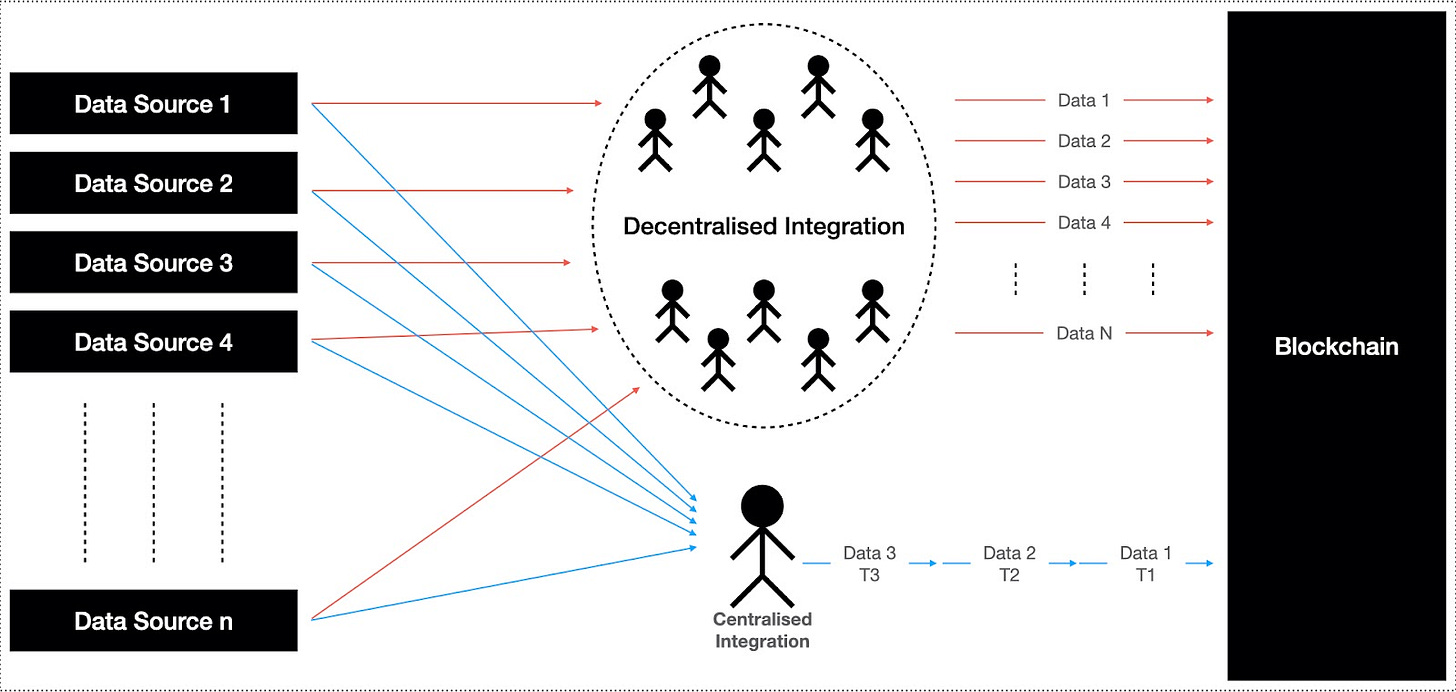
Centralized data integration limits oracle scalability and web3 growth
Oracles face a significant scalability challenge. Adding new data types or sources requires direct involvement from the oracle or protocol teams, creating a bottleneck that limits web3’s growth. With millions of potential data providers and use cases, relying on centralized teams to manually integrate and maintain each source is impractical and unsustainable.
The solution to this scalability problem is to decentralize data integration process, allowing third-party developers to build and manage these data providers. This would enable more scalable growth, where developers can freely add new data sources, reducing the burden on core teams and fostering innovation across the ecosystem.
Beyond data access web3 needs assurances of trust, provenance and integrity
As dApps advanced, it became clear that providing data’s value alone isn’t enough. Applications need assurances about the quality, source and integrity of the data they use. Key aspects include:
Provenance: Where does the data come from? Is the source reliable?
Integrity: Has the data been tampered with?
Correctness and Accuracy: Data should follow expected formats (correctness) and reflect real-world values (accuracy). For example, the price of Bitcoin must be represented correctly as 63500 not 100 or sixty-three thousand five hundred
Verifiability: Can the data’s origin, accuracy and integrity be verified trustlessly on-chain?
To address these needs, we evaluate data quality using the VIPCAP framework that we introduced which covers Verifiability, Integrity, Provenance, Correctness, Accuracy, and Private Data. This framework ensures that data is not only accessible but also reliable, private when necessary, and accurately reflects real-world states.
Despite the valuable role oracles have played in enabling decentralized applications, their limitations around data diversity, scalability and trust make it clear that a more robust solution is needed for web3 to fully evolve. While these limitations highlight the challenges faced by traditional oracles, they also underscore the need for a more robust solution.
DVPs bring secure verifiable web2 data to web3 enabling trustless and scalable dApps
DVPs are the next step in bringing web2 data to web3 using advanced technologies like Zero Knowledge Proofs(ZKP), Multi-Party Computation(MPC) and Fully Homomorphic Encryption(FHE) and leveraging internet standards like Transport Layer Security (TLS). DVPs ensure secure and verifiable data with guarantees of provenance, integrity and accuracy.
DVPs enable decentralized applications to handle private data safely, unlocking new possibilities for apps that require sensitive information like personal financial records, social reputation, etc. They also remove the need for centralized teams to manage data integration, making data handling more decentralized and scalable. Leveraging advanced cryptographic technologies they aim to achieve data properties like provenance, integrity and verifiability.
In the next sections we’ll explore DVPs in detail how DVP protocols work, project landscape and the different approaches they use to transform data in web3 followed by some real use cases and integrations by projects.
DVPs leverage advanced cryptography to form a secure and scalable architecture for web3
DVPs are advanced systems that securely bridge data from web2 to web3. They utilize TLS for secure transmission with a combination of ZKP for privacy, MPC for decentralized processing and TEE for secure hardware-based execution. These technologies ensure that data is secure, verifiable and trustlessly integrated into decentralized applications.
TLS secures most internet data making it essential for DVPs
TLS is a key protocol that secures most of the internet’s data, including web and email traffic. It ensures authenticity, correctness, accuracy and provenance of data, making it a reliable source for both centralized and decentralized applications.
Since TLS powers most online interactions, ensuring secure access to internet data. Protocols built on TLS allow web3 applications to import real-world data from web2 securely. For instance, an Uber driver could move their reputation to a new ride-hailing service without starting over.
While TLS is the underlying trust layer that ensures secure communication with web servers, different protocols leverage additional technologies to address the remaining challenges of data verifiability. This has led to multiple approaches which can broadly be categorized into three types: Proxy-based, MPC-based and TEE-based.
Before diving deep into each of these approaches and how they are shaping the future of web3, let's first explore the landscape of DVP protocols and Key Stakeholders.
DVPs rely on five stakeholders—Prover, Web Service, Notary, Verifier and Schema Builders
DVP involve five key stakeholders that ensure secure and verifiable data flow from web2 to web3:
Prover (Client): The prover or client, is the entity that initiates the process by proving the validity of off-chain data and bringing it on-chain with the help of the respective web service data schema integrated into the protocol.
Web Service: This is the TLS-based service where the user's data resides. It serves as the source of the data that the prover seeks to bridge to the blockchain.
Notary: The notary plays a critical role by collaborating with the prover, ensuring the correctness and integrity of the data being transferred. The notary is an active participant in the protocol and helps maintain trust throughout the process.
Verifier: The verifier is the entity that needs access to the data and, most importantly, must be able to trustlessly verify its origin, authenticity and integrity once it is brought on-chain.
Data Schema Builders: These are Devs that contribute to the protocols where they build and integrate Data Schemas into the protocol for users to use.
The three key approaches to DVP’s
Different DVP projects have emerged, each taking a unique path to leveraging the TLS standard. Broadly, there are three main approaches to DVPs:
MPC based approach
Proxy based approach
TEE based approach
These protocols share common goals but differ in how they handle key steps. Let’s dive into their common workflow step-by-step:
Step 1 - Establish TLS: Secure communication is initiated between the client and server.
Step 2 - Communicate: Data is exchanged as in any regular TLS interaction.
Step 1 & 2 takes place between Client and Web Server
Step 3 - Selective Reveal: Certain parts of the data or transaction are selectively exposed by the client based on the needs of the application.
Step 4 - Create Proof/Attestation: A cryptographic proof or attestation is generated to ensure data verifiability.
Steps 3 & 4 takes place between Client and Notary
Step 5 - Verify: The verifier (which could be a smart contract or decentralized network) confirms the authenticity of the proof.
Step 5 is done independently by Verifier.
The key differences between these protocols lie in how they manage the establishment of the TLS connection (Step 1) and the selective reveal of data (Step 3). These steps define the protocol’s strengths in privacy, trustlessness and security.
Before diving into the specifics, it’s important to note that each DVP approach—MPC-based, Proxy-based and TEE-based—offers unique solutions to the challenges of secure data verification. These methods differ in how they balance privacy, security and computational efficiency, making each approach suitable for different use cases in web3. Now, let’s explore the first approach: MPC-based.
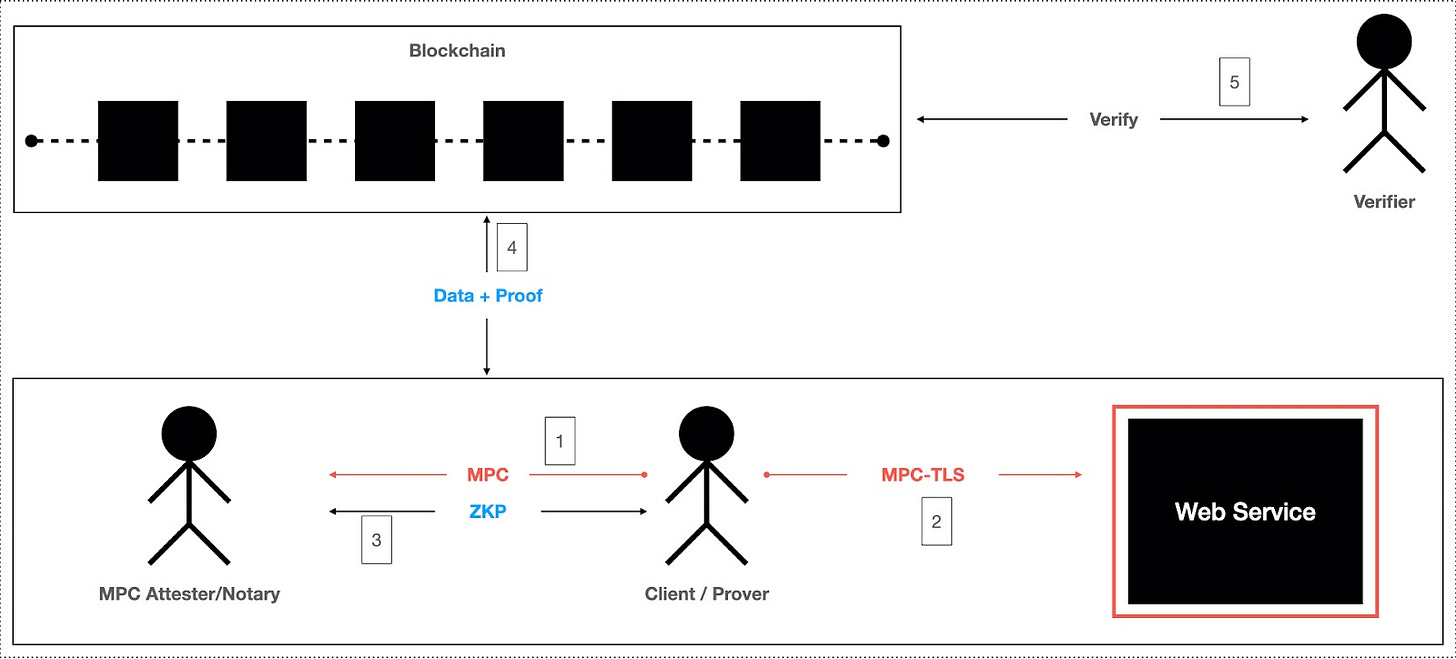
MPC-based approach provides robust security at cost of higher resource demands
In the MPC-based approach, the client collaborates with Notary(ies) to form a Multi Party network, which is used to establish MPC-TLS communication with the server. This setup allows both the client and notary to collectively perform secure operations without revealing any private data to each other. MPC-TLS ensures that the notary can monitor the client's actions while safeguarding the confidentiality of the client-server communication. The client's web server interactions are continuously verified by the notary, making the notary a critical part of the process.
The projects like Opacity Network, Primus Labs (prev. PADO), Vlayer and ZKON are building on this approach to leverage its high security and privacy standards for secure data verifiability in web3 applications.
The process of building data claims relies on ZKP, which provides a verifiable way to prove data integrity and authenticity without exposing the underlying information. A key advantage of the MPC-based approach is its robust security, powered by advanced cryptographic techniques like MPC and ZKP. This combination delivers high levels of privacy and trustlessness, with the server remaining unaware of the underlying MPC activities.
However, this approach comes with certain limitations. One risk is the potential for collusion between the client and the notary, which could result in the creation of false proofs. Moreover, MPC's computational and communication overhead is significant, potentially causing delays and even leading to TLS timeouts if the process becomes too slow.
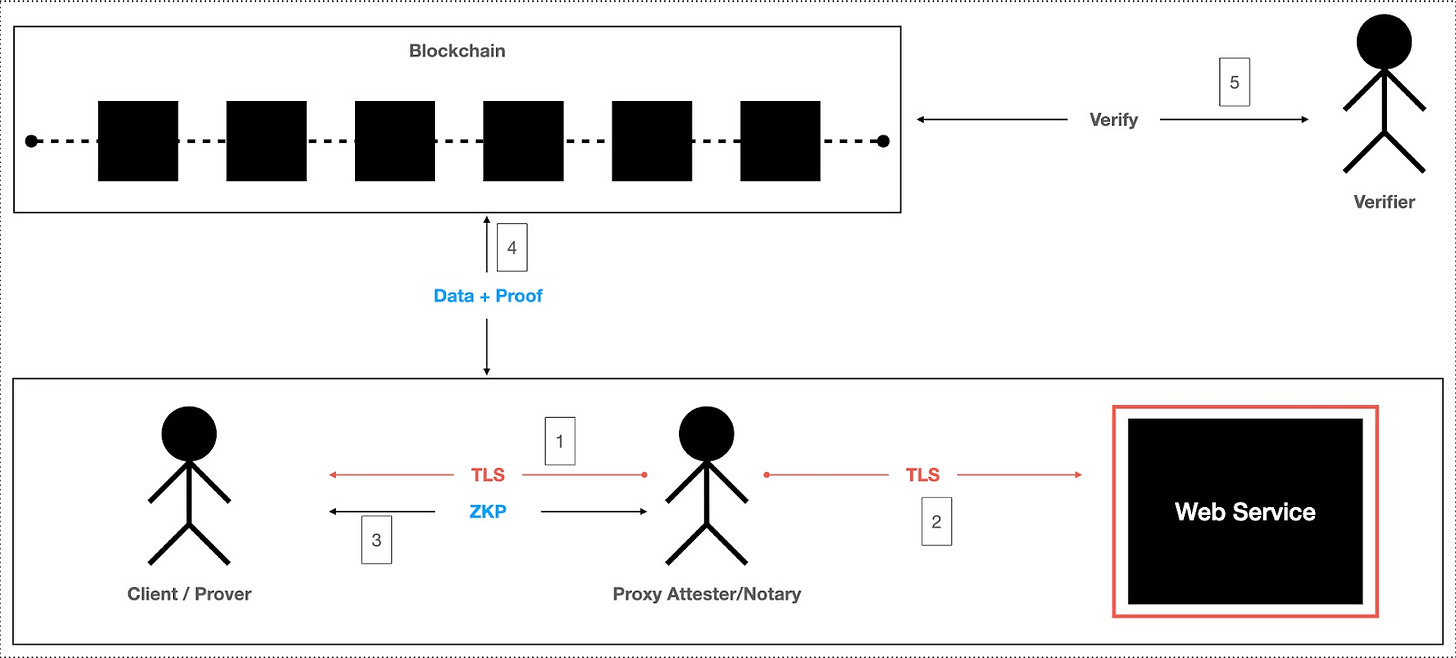
Proxy-based approach is simple but limited by centralization risk
In the proxy-based approach, the Notary acts as an intermediary between the client and the server, managing the communication flow. The notary forwards client requests to the server and relays the server’s responses back to the client. This approach leverages advanced TLS features, such as key updates, to maintain secure communication and enable selective data revelation. Additionally ZKPs are used to generate cryptographic proofs, while digital signatures provide attestation of the data's authenticity.
One of the main advantages of this approach is its simplicity. By avoiding the complexities of MPC, the proxy-based method is easier to implement and requires less computational overhead, resulting in better performance and lower resource consumption. However, there are significant drawbacks. The proxy can be blocked by the server, which undermines its reliability. Additionally, the risk of collusion between the proxy and the client poses a security concern, as it could lead to falsified data being transmitted and verified on-chain.
Projects like Reclaim Protocol and zkPASS are building on this approach to provide efficient and straightforward data verification solutions, leveraging its simplicity while addressing the inherent centralization trade-offs.
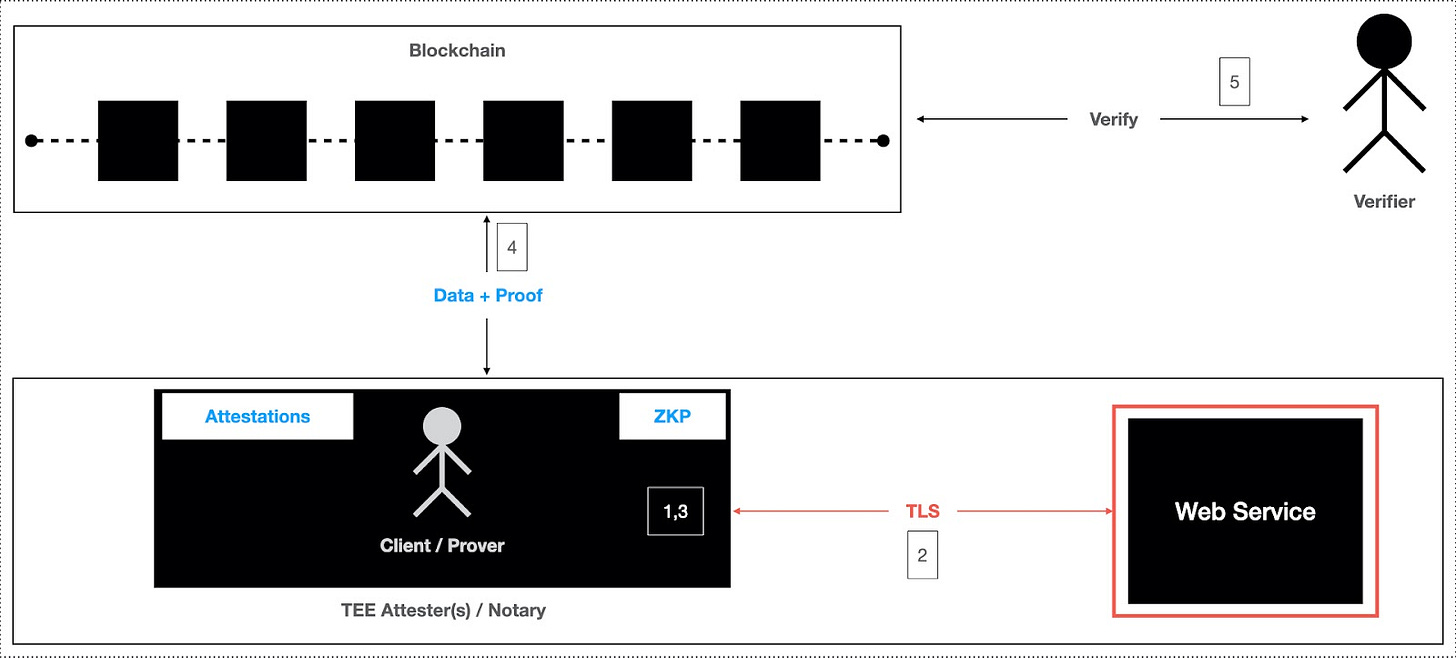
TEE-based approach provides high performance but dependent on hardware trust
In a Trusted Execution Environment (TEE) based approach, secure hardware enclaves such as Intel's SGX, AMD SEV and Amazon Nitro run the TLS protocol in an isolated environment, ensuring that client-server communication and data processing are protected from external tampering. TEEs provide a trusted environment that safeguards sensitive operations—even from system administrators—while generating attestation proofs and, in some cases, ZKP to verify that computations have been securely executed within the enclave.
The pros of the TEE-based approach include strong security and fast execution, while offering low latency and high efficiency by utilizing hardware capabilities. However, there are some significant cons to consider. The security of TEEs relies heavily on the trustworthiness of the hardware manufacturer, which can introduce centralization risks. If the hardware is compromised or has vulnerabilities, the entire system's security could be at risk. Additionally, TEEs lack transparency, as the inner workings of the enclave are not visible to external parties, making it difficult to independently verify the integrity of operations—potentially raising concerns in decentralized systems that prioritize trustlessness and openness.
The projects like Turnkey and Clique leverage the TEE-based approach to deliver high-performance, secure data verifiability solutions, capitalizing on the efficiency of hardware while carefully navigating its trust limitations.
DVP landscape is expanding rapidly
Each of these approaches—MPC-based, Proxy-based and TEE-based—solves specific challenges in ensuring data integrity, security and scalability. By leveraging these techniques, DVPs provide the foundation for real-world applications that need verifiable data from both public and private sources. These solutions aren't just theoretical; they are actively being integrated into diverse web3 use cases, enabling new capabilities in sectors such as identity verification, DeFi, gaming and social networks. Let’s now explore how DVPs are powering innovative use cases across a variety of industries.
Real-World Use Cases Show How DVPs Unlock web3's Full Potential
DVPs simplify identity and onboarding thus bringing web2 credentials, reputations, and work experience into web3
Seamless identity verification and onboarding are critical for expanding web3 adoption, and several projects are tackling this challenge head-on. Turnkey integrates familiar web2 credentials like Google, Facebook, and Apple Oauth to allow users to access non-custodial wallets without prior knowledge of crypto. This significantly lowers the entry barrier for new web3 users, bridging the gap between web2 and web3.
Similarly, NoshDelivery leverages the Opacity Network to enable drivers and restaurants to export their reputations from web2 food delivery platforms into a unified web3 framework. This approach merges the best of both worlds, enabling reputation portability while enhancing user trust and retention across platforms. In the web3 gaming space, Clique is employed by Privado.ID to integrate self-sovereign identity and privacy technologies, ensuring a secure and bot-free gaming experience by protecting users’ identities and keeping their data private while engaging in blockchain-based games.
Professional networks are also utilizing DVPs to verify work experience and skills. On-chain professional networks platforms like Icebreaker and Bondex use Reclaim to provide verifiable proof of work for user profiles. By bringing work credentials on-chain, these platforms enable trustless and verifiable job matching and career advancement in the decentralized economy.
DVPs strengthen on-ramps and digital marketplaces with verified identities and secure transactions
DVPs play a crucial role in web3’s growth by enhancing both crypto on-ramp solutions and digital asset marketplaces with verified identities and secure transaction frameworks. Projects like P2PX and zkMe leverage Reclaim Protocol to securely onboard new users: P2PX uses India’s Aadhar portal to enable smooth, compliant crypto transactions in INR, while zkMe integrates verified credit scores in a privacy-preserving way, allowing users to participate in decentralized applications with confidentiality.
Similarly, in digital marketplaces, verified identities and secure transactions are essential. zkp2p, a consumer goods marketplace, uses Reclaim’s TLSProxy to verify users through platforms like Ticketmaster, helping to ensure authenticity and reduce fraud. Meanwhile, Kinto, in partnership with Turnkey, brings TradFi-level KYC standards to web3, offering KYC-verified wallets for compliant and sybil-resistant participation in DeFi.
DVPs bring trust and verifiability to AI, Social Finance and Marketing
The social finance and marketing need trust and verifiability to incentivise participants on the marketing efforts. Influencer marketing industry for example is embracing web3 through projects like Daisy, which uses the Opacity Network to verify influencers’ social identities and campaign activities. By ensuring the authenticity of performance metrics and tracking campaign-related activities, Daisy helps brands incentivize influencers in a transparent and verifiable way, ensuring trust between parties.
Meanwhile in AI, Primus utilizes its DVP technology to generate verifiable proofs of ChatGPT conversations. This capability can unlocks novel applications like verifiable consulting services, secure AI-driven customer support and tamper-proof dispute resolution to list a few. By bridging AI with blockchain, apps ensures that AI-generated outputs can be trusted and verified without compromising user privacy, adding a new dimension to web3 innovation.
DVPs boost prediction markets by providing secure verifiable results
Prediction markets, which require secure, real-time data, benefit immensely from DVPs. Satoshi’s Palace, a gaming platform, uses Reclaim Protocol’s zkFetch to securely retrieve Bitcoin price data from sources like CoinMarketCap and prove its authenticity on-chain. This enhances trust within the platform by ensuring that the data being used for gaming outcomes is accurate and verifiable.
Similarly, Fr.Market, a prediction market integrates Reclaim’s zkFetch to bring YouTube Music chart stats on-chain, allowing users to predict which music videos will top the charts. This combination of entertainment and decentralized prediction markets opens up new possibilities in blockchain-based user engagement.
DVPs enhance gaming and social dApps by ensuring security and sybil resistance
Gaming and social platforms are integrating DVPs to ensure Sybil resistance and protect user identities. Lens and Phaver rely on Clique to verify users by analyzing off-chain social data from platforms like Twitter, improving user trust and reducing fake accounts. On the gaming side, Ronin uses Clique to process off-chain gaming data, enabling identity-based rewards while maintaining privacy, providing a secure way to bring gaming achievements on-chain.
Meanwhile, CatOff, a peer-to-peer wager platform, uses Reclaim to prove the results of activities such as steps tracked, Twitter impressions, or GitHub commits, ensuring that wagers are settled fairly based on verifiable, digital results.
DVPs enable secure tokenization in DePIN and real-world assets
In the realm of decentralized physical infrastructure networks (DePIN) and real-world asset tokenization, eGrain leverages ZKON’s blockchain and IoT solutions to tokenize agricultural commodities. This enables real-time data verification and secure asset tokenization, ensuring that the commodities remain authenticated throughout their lifecycle.
Similarly, Codedestate, a real-estate tokenization platform, uses Reclaim Protocol to verify land ownership in Dubai through secure, verifiable integration with government land portals, allowing real estate transactions to be conducted on-chain with full confidence in data authenticity.
DVPs are the ‘super oracles’ powering the next wave of dApp innovation
DVPs are not just another technical advancement—they are the next frontier in unlocking web3’s full potential. Traditional oracles were essential for web3’s early growth, but they’ve hit a ceiling when it comes to scalability, privacy and trust. DVPs are a super set of oracles that solve these critical issues offering trustless, verifiable and scalable ways to integrate real-world data public and private into decentralized systems. This marks a transformative shift, especially for applications requiring private data, which oracles simply cannot handle securely.
Most exciting thing about DVPs is the real-world applications it unlock—from under-collateralized DeFi to Social apps and enterprise adoption. These protocols are creating new opportunities by ensuring that data can be trusted and verified without relying on centralized entities. This is the key to mainstream adoption, not just in web3 but web2 and across industries like finance, supply chain and identity verification.
DVPs are the cornerstone of the next phase of web3 evolution. As more projects and developers embrace these protocols, they will pave the way for a more transparent, efficient and secure decentralized internet—setting the stage for the next wave of innovation and growth. For those of us watching the space closely, DVPs are more than a solution—they're the foundation of the future of web3.
We express our gratitude to Madhavan from Reclaim Protocol, Xiang from Primus Labs, and Gabi from ZKON for generously sharing their valuable insights, which have been integrated into this article.